
The UNESCO training manual for the protection of the underwater cultural heritage in Latin America and the Caribbean

The Practical Psychic Self-Defense Handbook: A Survival Guide: Bruce, Robert: 9781571746399: Amazon.com: Books

Gotta Catch 'Em All: Understanding How IMSI-Catchers Exploit Cell Networks | Electronic Frontier Foundation

Political Parties Playbook: A Guide for Digitizing Party Operations | International Republican Institute

Countering Swarms: Strategic Considerations and Opportunities in Drone Warfare > National Defense University Press > News Article View

Detecting Biothreat Agents: From Current Diagnostics to Developing Sensor Technologies | ACS Sensors
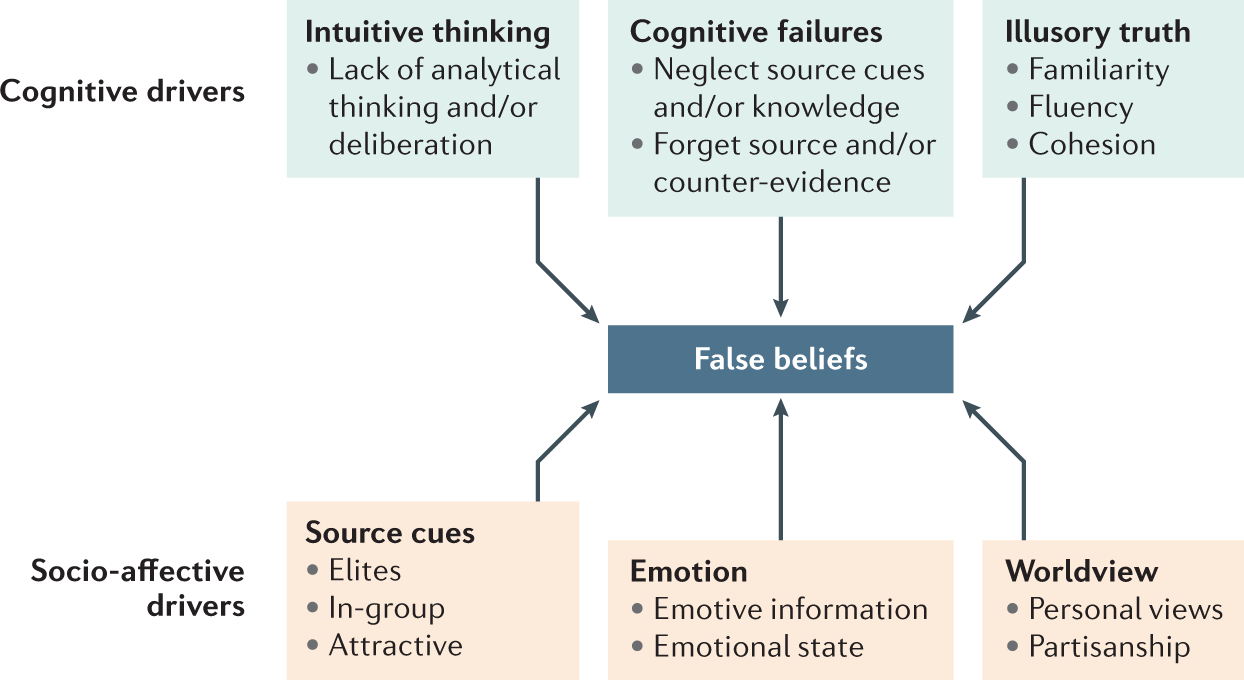
The psychological drivers of misinformation belief and its resistance to correction | Nature Reviews Psychology

The Memory of the World in the digital age: digitization and preservation; an international conference on permanent access to digital documentary heritage
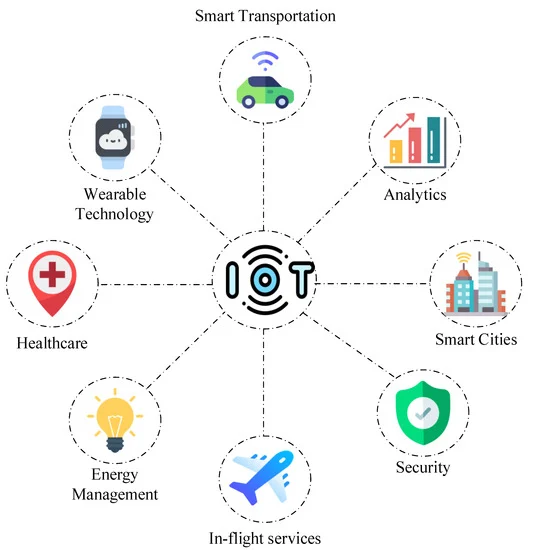
Sustainability | Free Full-Text | State-of-the-Art Review on IoT Threats and Attacks: Taxonomy, Challenges and Solutions
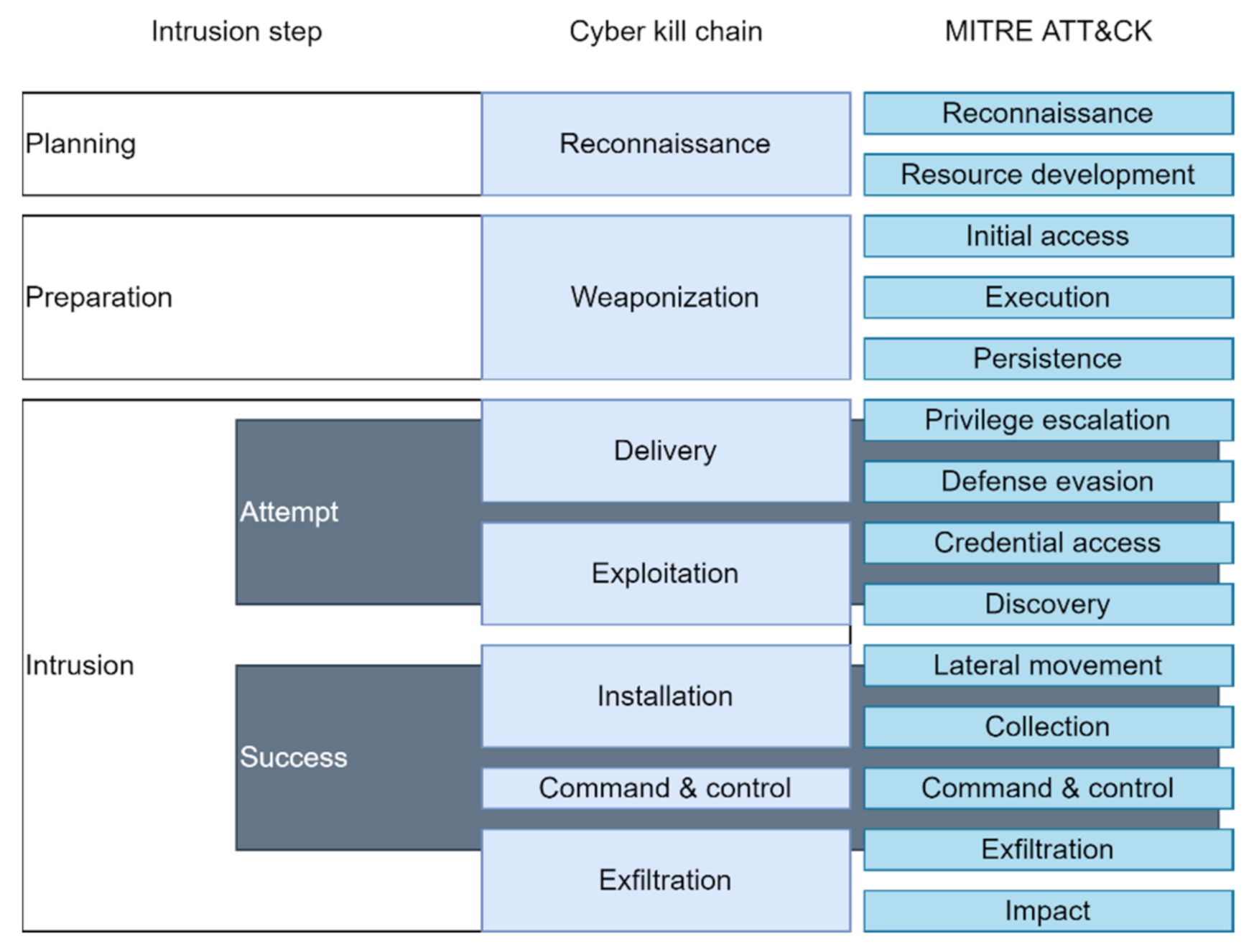
Sensors | Free Full-Text | Cyberattack Models for Ship Equipment Based on the MITRE ATT&CK Framework

Introduction of 《Inside Radio: An Attack and Defense Guide》 – 雪碧0xroot | RadioHub | IoT RF Hardware Hacking | 博观而约取厚积而薄发







![Inside Radio: An Attack And Defense Guide [PDF] [4223clofej90] Inside Radio: An Attack And Defense Guide [PDF] [4223clofej90]](https://vdoc.pub/img/crop/300x300/7h70qulend40.jpg)




